Experimenting with FIDO2 Key with Azure Active Directory
I have always wanted to experiment with FIDO2 key with Azure Active Directory and I recently stumbled upon an affordable FIDO2 key on Amazon for $25 with next day delivery.
It is called HyperFIDO Pro Titanium and made by a company called Hypersecu. Researching on their website and I discovered that HyperFIDO Pro is Microsoft approced and AAD ready. So I cant resist but to buy it. Here’s the product link HyperFido Titanium Pro.
Let’s have fun!
Navigate to Azure Active Directory
Head down to Security > Authentication Methods > Policies
Enable FIDO2 Security Key
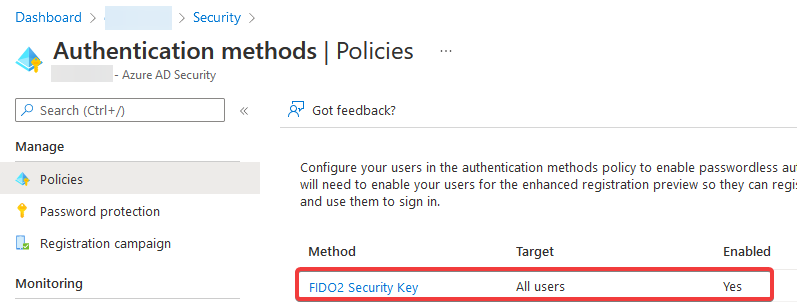
That’s it! And now you are ready to register the key by going to MFA Setup.
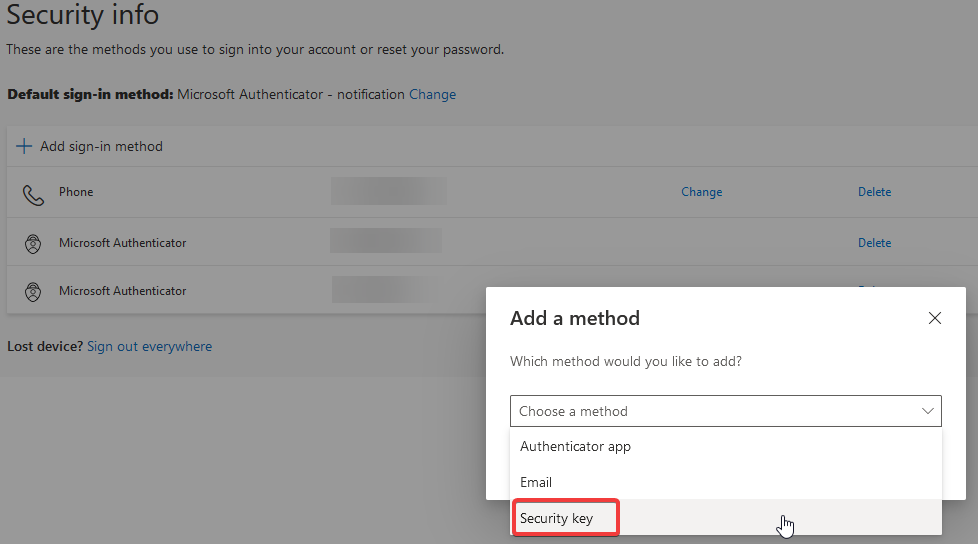
Click Add Sign-in method and select Security Key
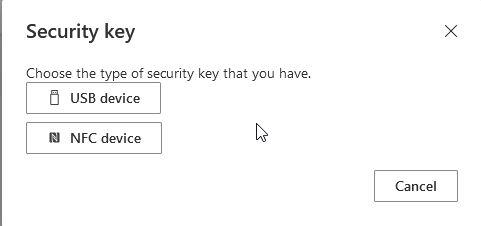
Select the device accordingly, in my case here it’s USB Device
Ready your key, remove it from the packaging!
It passes it to Windows Security
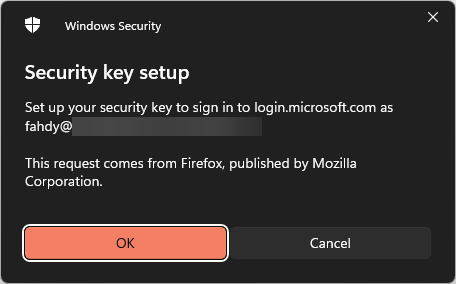
Some warning.
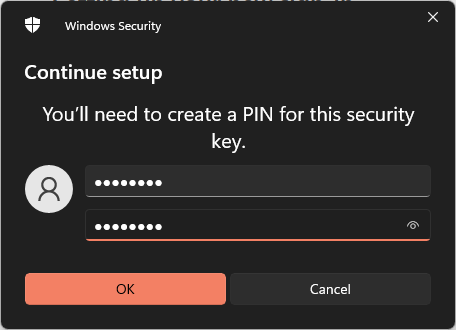
Supply PIN numbers to protect the key
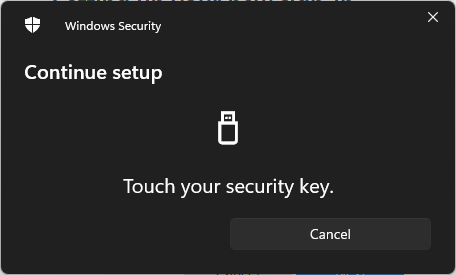
Touch your security key
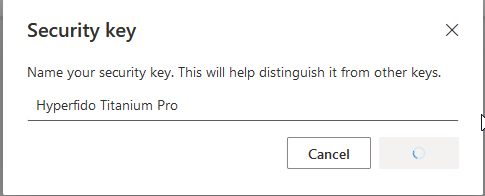
Give it a name
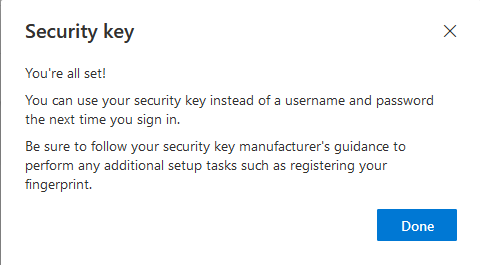
Congrats! You’ve done it!
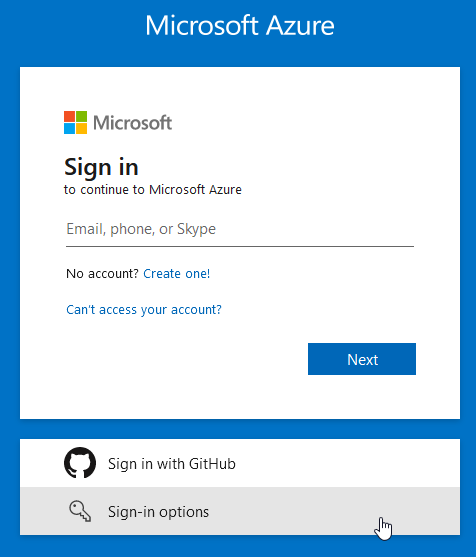
Now let’s test the key on an Incognito/Private web browser window and navigate to Azure Portal.
Then instead of typing your login email address as you normally would, go and click Sign-in options
Select Sign in with Windows Hello or a security key

That’s it for the web use.
However, you can take it further by allowing your AAD joined and Hybrid AAD joined devices to use the same security key to sign in to the computer.
Essentially you go to Microsoft Endpoint Manager Admin Centre and create a configuration profile > Windows 10 and later > Templates > Identity Protection > enable Use security keys for sign-in.
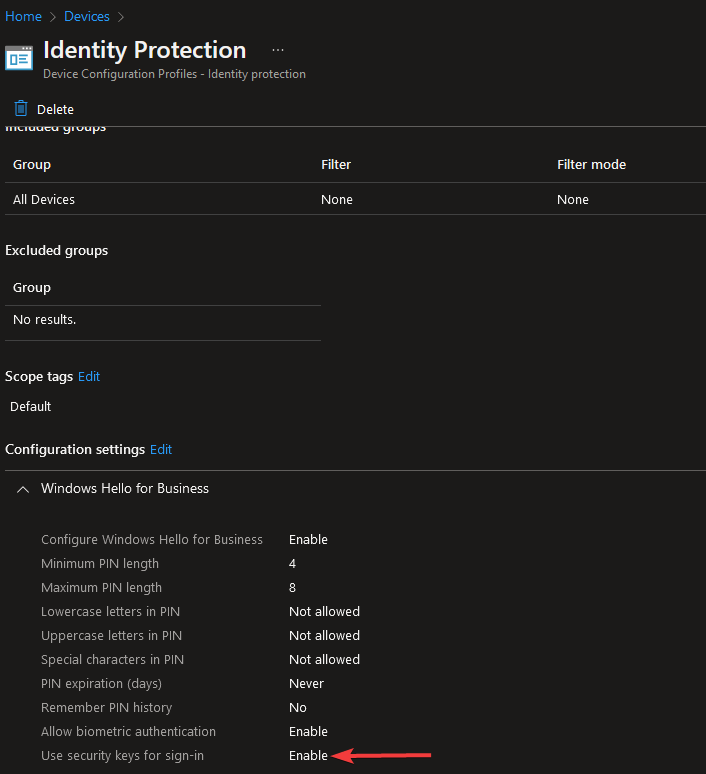
Wait for the configuration to come down, you may need to restart your computer before the option becomes available.
Well done you!